Navigation
Related Post
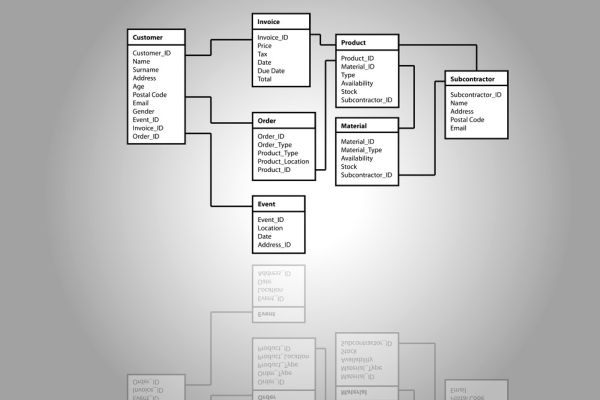
Database Access
Database access refers to the methods and technologies used to retrieve, update, or delete data stored in a digital database. This access is controlled and managed to ensure data accuracy, security, and availability across software applications and systems.
Most modern applications rely on some form of database access to function correctly, whether it’s a website displaying product information or an app saving user preferences. The way data is accessed can range from simple queries in a spreadsheet-like environment to complex instructions in programming languages. Managing who can access what data, how often, and in what way is central to how organizations maintain data consistency and security.
Methods of Access
Database access can happen directly through structured queries or indirectly through applications. The most common way to access data is through the use of SQL (Structured Query Language), which enables users to search for, modify, or insert data into a database table. This is often done within database management tools such as Microsoft SQL Server Management Studio, Oracle SQL Developer, or MySQL Workbench.
In many cases, end users never interact with the database directly. Instead, software applications access the database in the background through code written in programming languages such as Java, C#, or Python. This indirect access is managed using specialized tools, such as database drivers or APIs, like ODBC and JDBC, which help connect programs to the database.
Access Control and Permissions
Controlling who can access which parts of a database is critical for maintaining security and privacy. Role-based access control (RBAC) is a standard method where users are assigned roles that determine their level of access. For instance, one person might be allowed to view data, while another can edit or delete it.
Database administrators configure access rules through user accounts, permissions, and security settings. These settings are part of the database management system (DBMS), which helps enforce security policies, track user activity, and prevent unauthorized access or data breaches.
Application Integration
Most software applications depend on database access to store and retrieve information as part of their everyday operations. This integration is built into the application’s architecture, allowing functions such as login validation, inventory lookups, and user interactions to occur seamlessly behind the scenes.
Application developers use frameworks such as Entity Framework, Hibernate, or Spring Data to simplify the process of connecting and interacting with databases. These tools reduce the amount of manual SQL code needed and help manage data operations efficiently within the application logic.
Performance Considerations
Accessing a database quickly and efficiently is crucial, especially when large volumes of data are involved or multiple users are connected simultaneously. Poorly optimized queries or excessive data requests can slow down an entire system. To address this, developers and database professionals employ techniques such as indexing, caching, and query optimization.
Performance tools within a DBMS help identify slow queries or resource bottlenecks. For example, SQL Server includes a Query Analyzer, while Oracle provides tools like SQL Tuning Advisor. These help diagnose issues and improve response times for database operations.
Remote and Cloud Access
Database access is no longer limited to local networks or on-premises systems. Many databases are now hosted in the cloud using services like Amazon RDS, Microsoft Azure SQL Database, or Google Cloud SQL. These platforms allow access from virtually anywhere, increasing flexibility and scalability.
Cloud-based database access often includes additional security features such as encryption, multi-factor authentication, and network firewalls. These tools help protect data even when it is accessed remotely, making modern cloud databases both powerful and secure.
Conclusion
Database access is a fundamental component of how information systems operate in the modern world.
By managing who can retrieve or modify data, how applications interact with databases, and how performance is maintained, organizations can ensure that data remains reliable, accessible, and secure for everyday use.
What is SQL? – 5 mins
